dumbpasswordrules.com
Cigna - Dumb Password Rules
A max of 12 characters... Can't handle most symbols (only 5 supported). At least they have two factor auth via email or sms **sigh**
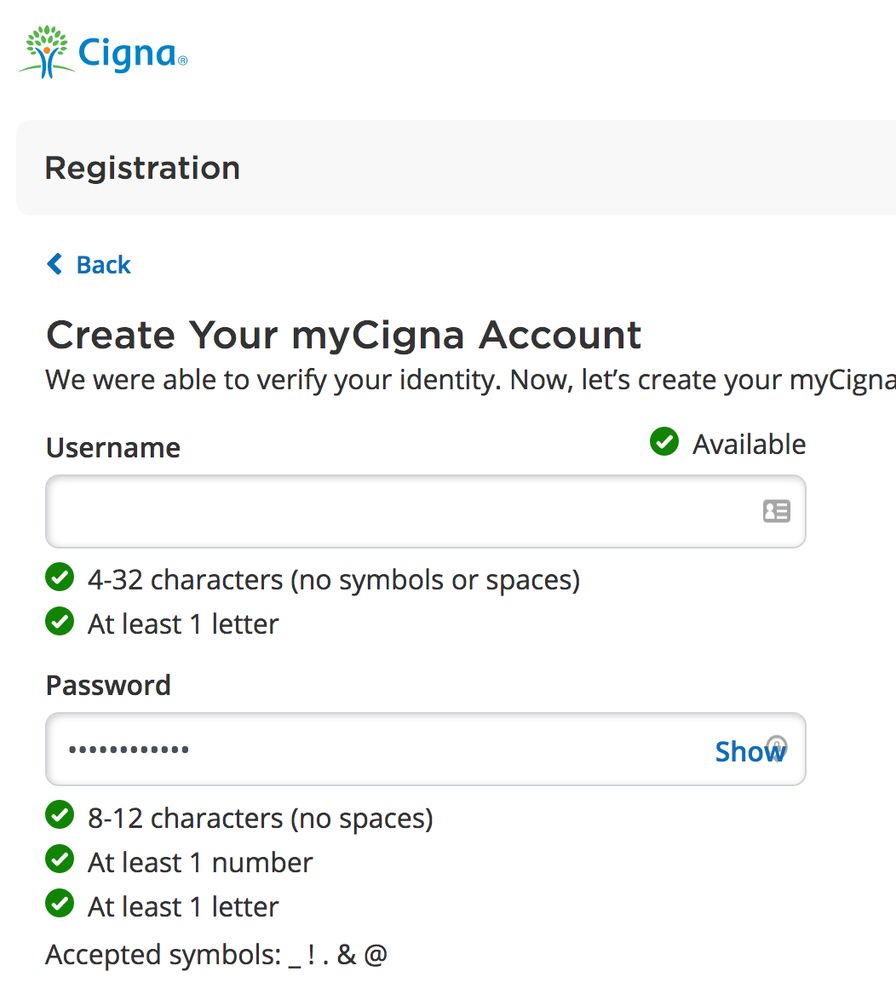
dumbpasswordrules.com
Cigna - Dumb Password Rules
A max of 12 characters... Can't handle most symbols (only 5 supported). At least they have two factor auth via email or sms **sigh**


dlvr.it
Toxic trend: Another malware threat targets DeepSeek
Introduction DeepSeek-R1 is one of the most popular LLMs right now. Users of all experience levels look for chatbot websites on search engines, and threat actors have started abusing the popularity of LLMs. We previously reported attacks with malware being spread under the guise of DeepSeek to attract victims. The malicious domains spread through X posts and general browsing. But lately, threat actors have begun using malvertising to exploit the demand for chatbots. For instance, we have recently discovered a new malicious campaign distributing previously unknown malware through a fake DeepSeek-R1 LLM environment installer. The malware is delivered via a phishing site that masquerades as the official DeepSeek homepage. The website was promoted in the search results via Google Ads. The attacks ultimately aim to install BrowserVenom, an implant that reconfigures all browsing instances to force traffic through a proxy controlled by the threat actors. This enables them to manipulate the victim’s network traffic and collect data. Phishing lure The infection was launched from a phishing site, located at https[:]//deepseek-platform[.]com. It was spread via malvertising, intentionally placed as the top result when a user searched for “deepseek r1”, thus taking advantage of the model’s popularity. Once the user reaches the site, a check is performed to identify the victim’s operating system. If the user is running Windows, they will be presented with only one active button, “Try now”. We have also seen layouts for other operating systems with slight changes in wording, but all mislead the user into clicking the button. Malicious website mimicking DeepSeek Clicking this button will take the user to a CAPTCHA anti-bot screen. The code for this screen is obfuscated JavaScript, which performs a series of checks to make sure that the user is not a bot. We found other scripts on the same malicious domain signaling that this is not the first iteration of such campaigns. After successfully solving the CAPTCHA, the user is redirected to the proxy1.php URL path with a “Download now” button. Clicking that results in downloading the malicious installer named AI_Launcher_1.21.exe from the following URL: https://r1deepseek-ai[.]com/gg/cc/AI_Launcher_1.21.exe. We examined the source code of both the phishing and distribution websites and discovered comments in Russian related to the websites’ functionality, which suggests that they are developed by Russian-speaking threat actors. Malicious installer The malicious installer AI_Launcher_1.21.exe is the launcher for the next-stage malware. Once this binary is executed, it opens a window that mimics a Cloudflare CAPTCHA. The second fake CAPTCHA This is another fake CAPTCHA that is loaded from https[:]//casoredkff[.]pro/captcha. After the checkbox is ticked, the URL is appended with /success, and the user is presented with the following screen, offering the options to download and install Ollama and LM Studio. Two options to install abused LLM frameworks Clicking either of the “Install” buttons effectively downloads and executes the respective installer, but with a caveat: another function runs concurrently: MLInstaller.Runner.Run(). This function triggers the infectious part of the implant.private async void lmBtn_Click(object sender, EventArgs e) { try { MainFrm.c__DisplayClass5_0 CS$8__locals1 = new MainFrm.c__DisplayClass5_0(); this.lmBtn.Text = "Downloading.."; this.lmBtn.Enabled = false; Action action; if ((action = MainFrm.O.__Run) == null) { action = (MainFrm.O.__Run = new Action(Runner.Run)); #

cyberlens.beehiiv.com
Cracked at the Core: How Ransomware Gangs Exploit SimpleHelp Flaws for Double Extortion Schemes
Inside the Tactical Playbook of Threat Actors Weaponizing Remote Access Software Vulnerabilities to Orchestrate Multi-Layered Extortion Campaigns

www.bleepingcomputer.com
Microsoft creates separate Windows 11 24H2 update for incompatible PCs
Microsoft confirmed on Tuesday that it's pushing a revised security update targeting some Windows 11 24H2 systems incompatible with the initial update released during this month's Patch Tuesday.


innovirtuoso.com
How to Protect Your Environment from the NTLM Vulnerability
Discover the risks associated with NTLM vulnerabilities and learn effective strategies to mitigate them. This blog post discusses the importance of auditing
www.wired.com
RFK Jr. Orders HHS to Give Undocumented Migrants’ Medicaid Data to DHS
Plus: Spyware is found on two Italian journalists’ phones, Ukraine claims to have hacked a Russian aircraft maker, police take down major infostealer infrastructure, and more.

www.bleepingcomputer.com
Brute-force attacks target Apache Tomcat management panels
A coordinated campaign of brute-force attacks using hundreds of unique IP addresses targets Apache Tomcat Manager interfaces exposed online.

dlvr.it
All’s Not Quiet on the Western Front: Increasingly hostile behaviour in cyberspace tests coalitions of the willing :
The UN Open-Ended Working Group on ICTs has come a long way in defining the threats to international peace and security with explicit references to parts of critical infrastructure, impacts on targeted organisations and affected citizens, and responses formed along coalitions of States and stakeholders working toward improved accountability and resilience. Yet, the recent public attributions inside and outside the plenary invite a question of whether the policy of ‘naming and shaming’ has ever been effective while like-minded groups face growing internal friction. Blame game The penultimate meeting of the UN Open-Ended Working Group on ICTs (OEWG) took place in February, shortly before the third anniversary of the full-scale invasion of Ukraine. Many, primarily European, delegations confronted Russia with interventions highlighting the country’s continued aggression. The European External Action Service noted the impact of Russia-affiliated actors directly targeting the European Union and its Member States, detailing the early January 2025 incident when a suspected ransomware attack targeted the offices of the Slovak land registry. This malicious cyber incident suspended public cadastre services nationwide and directly impacted other sectors such as banking, construction, and agriculture. This statement aligned with an earlier Estonian attribution of cyberattacks against domestic government entities, after a joint investigation established that Russia’s military intelligence service (GRU) was behind the 2020 incident aimed at damaging national computer systems and accessing sensitive information. Ukraine aligned with the European Union and highlighted the rise in cyberattacks targeting political and electoral processes, public institutions and vital services, including health and energy facilities. Ukraine has faced constant streams of Russia’s malicious cyber activity aimed at supporting kinetic operations, damaging national digital ecosystems and cyber capabilities, and destabilising Ukraine’s allies and partners in the cyber domain. Russia, in return, accused Ukraine of interference in the digital infrastructure of NATO Member States and claimed evidence in a recent example of a massive cyberattack on the Slovak national insurance company. Slovakia retorted that such an attack did not take place. Instead, the national authorities recorded a medium-sized phishing campaign against the national health insurer conducted from Russian servers. A notable silence on the anniversary came from the U.S., which did not mention or condemn Russia, and focused the intervention on malicious Chinese actors. This further underscored a recent trend toward specific attack descriptions and direct references to the perpetrators, as much as demonstrated a shift in U.S. foreign policy. The U.S. delegation called out Chinese pre-positioning in critical infrastructure, zooming on the recent extensive compromise of the national telecommunication networks, one of the nationally declared sixteen critical sectors. According to the U.S., Chinese hackers accessed employee workstations and unclassified documents. This public attribution linked the observed malicious activity to the Chinese government and described a larger pattern allowing China to launch disruptive cyberattacks in the event of a major crisis or conflict, such as the potential military activities in Taiwan, inducing societal panic and harming civilians. This statement ensued mutual accusations of pre-positioning in each other’s networks––China denied involvement, disputed the evidence leading to associations with State-supported activity, and objected to the U.S. policy of cyber deterrence as well as alleged use of offensive cyber capabilities against critical infrastructure. Lebanon earlier attributed attacks using booby-trapped pagers, designed and constructed with explosives while being disguised as apparently harmless portable devices, to Israel. The exploding pagers caused panic across the country and compromised the security of Lebanese ICT supply chains. In a separate case in December, Israel was blamed for jamming GPS systems in Lebanon and spoofing satellite signals used by civilian aircraft, thereby endangering civilian aviation. Israel responded by denying the allegations, instead attributing the incident to Hezbollah sponsored by Iran and asserting that the organisation exploits civilian infrastructure. Iran faced further pressure from the U.S. in February, asserting that Iran-affiliated actors targeted Israel-made technology and affected domestic water and wastewater systems considered critical. Iran called on delegations to observe the principle enshrined in the UN General Assembly resolution 73/27, which demands that accusations brought against States in organising or committing wrongful acts are substantiated. However, in the same breath, the statement concluded by blaming the U.S. for supporting and facilitating recent attacks on industrial infrastructures, such as steel and petrochemical industries, gas stations, and municipal public services systems. The two recent rounds of OEWG negotiations have highlighted that publicly attributing attacks with evidence and specifications of which norms or laws have been violated remains a tool for States to advance accountability. This particularly applies to the growing trend of joint public attributions, especially when those are part of a larger set of tools and followed by joint action. These statements also serve to inform the international community and signal to the adversary that a State has observed malicious activity. However, the intensifying accusations raise questions about the effectiveness of ‘naming and shaming’ in the plenary if everyone has already been named and no one seems to be ashamed. A brief account of the long history of cyber threats Despite the steep growth in frequency, scale, and severity of ransomware attacks, only the latest progress report in July 2024 reached a consensus on referencing the resulting harm, disruption of essential services to the public and the imminent impact on international peace and security. Still, several States, particularly those known for providing sanctuary jurisdictions for cybercriminal groups, loudly objected to considering ransomware in the interim reports. The cyber threat landscape has continued to deteriorate, with a large number of threat actors conducting exploitative and aggressive operations and the criminal model of hiring ransomware attacks as a service. The tone, scope, and depth of discussed threats have reflected these shifts, and the recent sessions have seen more emphasis on ransomware, especially when targeting medical facilities, undersea cables, and humanitarian organisations. Several delegations further noted a rise of hacktivist groups with demonstrated sophisticated capabilities, the increasing use of cryptocurrencies to support illicit activities, and the pervasiveness of commercial spyware facilitating human rights abuses. The Group has come a long way in recognising new and emerging technologies, including quantum computing and artificial systems, their ever-evolving properties and characteristics that could create new vectors and vulnerabilities in the digital systems, increase the speed and enhance the targeting potential of malicious cyber activity. Kazakhstan, for example, spoke about the dual-use nature of Artificial Intelligence (AI), which requires stronger regulatory frameworks, global collaboration, and the development of ethical guidelines to ensure such technology is used responsibly. El Salvador stressed the need for protecting privacy in AI models, and the threat of AI enabling autonomous decision making and actions, and the potential impacts of quantum computing on cryptographic standards. To identify the scope of discussions, Canada submitted a non-paper proposing to focus on AI-enabled cyber threats, cyber threats that target AI systems, and how AI can be used to prevent, mitigate and defend cyber threats. Another area of progress has been more transparent designations of critical infrastructure when calling out malicious behaviour targeting such networks, facilities, or services. For instance, cyber incidents affecting the healthcare sector have been constantly in the spotlight. Increased attention came in response to the UN Security Council meeting in November 2024, which focused on surging ransomware attacks against healthcare, highlighting that cyberattacks routinely breach the confidentiality and integrity of medical data and undermine trust in the health systems, delay hospital treatments and disrupt broader biomedical supply chains. Many countries have also come forward to highlight specific needs. The Pacific Islands Forum brought up a regional issue of ICT connectivity being impacted by climate change. Vanuatu highlighted the importance of securing maritime cables against malicious activity, which could cause significant damage or disrupt countries' participation in the digital economy. The EU delegation stressed several recent undersea cable incidents in the Baltic Sea, underlining the importance and urgency of addressing the physical safety of critical cyber infrastructure. Delegations further discussed horizontal and vertical threats, including the cascading effects of cyberattacks on interconnected sectors and suppliers. These risks are compounded by increasing vulnerabilities among manufacturers, particularly as supply chain attacks rise. The threat intensifies when compromised products reach end-users. Not only specific threats and sectors but also aggravating circumstances, such as situations of armed conflicts, were elaborated by the Group, with an emphasis on the humanitarian sector being under intensified attacks. The International Committee of the Red Cross and many other humanitarian and international organisations have been targeted by malicious cyber activities, ranging from cyber operations disrupting their operations to disinformation campaigns. This has been reflected in the shared concern among delegations, recognising that threat actors can disrupt the ability of humanitarian organisations to conduct their work in a safe, secure and independent manner, and undermine trust in humanitarian work. While important, these discussions will need to be marked in the final consensus report to provide for a lasting impact. Coalitions of the willing show first cracks The recent sessions have featured growing references to accountability, either as a subject in itself or in describing specific measures and tools, prominently sanctions. In February, Australia imposed additional cyber sanctions in response to the 2022 cyberattack against the country’s largest private health insurance provider, Medibank Private. The United Kingdom and the U.S. have also imposed sanctions on these malicious cyber actors, demonstrating a collective resolve. States have increasingly introduced cyber sanctions regimes to prevent, discourage, deter, and respond to malicious cyber activities. The European Union follows the cyber diplomacy toolbox, while the United Kingdom and the U.S. governments maintain a list of designated targets subject to cyber sanctions. The latter is leading with over three hundred cyber sanctions highly concentrated on a few countries, with Russia, Iran, and North Korea being the primary targets. Coalitions of the willing, joining attributions and sanctions, information sharing and operational and policy initiatives, have grown increasingly influential, outpacing the progress achieved in UN deliberations. The Pall Mall Declaration, initiated by the United Kingdom and France in February 2024, gathered dozens of states, industry actors, civil society, and academia representatives in London to tackle the proliferation and commercialisation of cyber intrusion tools, primarily spyware. This process acts as a confidence-building measure, helping to promote best practices through the exchange of views, information sharing, and strengthening public-private sector partnerships and cooperation. While state-led, the Pall Mall Process supports stakeholder participation and released a consultative report on good practices for commercial cyber intrusion capabilities addressed to vendors and States. In November 2024, the Paris Peace Forum hosted a meeting of the Pall Mall Process and the annual conference returned to Paris in April to launch a Code of Practice for States. The International Counter Ransomware Initiative has been hailed as a major success, offering a more effective approach to international cooperation of countries willing to proactively tackle ransomware. The fourth summit was held last October and hosted sixty-eight countries and organisations. While the initiative has become self-sustaining with support from the many members taking on leading roles, it is a White House project, and the U.S. influence and leadership may not be easily duplicated. The seismic shifts in the country’s foreign and cyber policies have introduced uncertainty to the Counter Ransomware Initiative and other longstanding partnerships, notably Five Eyes. The intelligence alliance, comprising Australia, Canada, New Zealand, the United Kingdom, and the U.S. has lately faced internal strains and a series of political and strategic divergences among its members such as those following the Trump administration’s decisions to temporarily suspend intelligence sharing with Ukraine. The UN remains the most inclusive platform for the international community to exchange views on existing and emerging threats and achieve incremental but important progress in the future permanent mechanism. However, due to its many limitations, including difficulty reaching consensus among Member States and a history of injudicious use of veto powers, coalitions of the willing remain the perspective way to advance cyber accountability and resilience. The rules-based order will depend on the resolve of Western like-minded countries to form an influential enough community that can demand compliance and foster responsibility.