dumbpasswordrules.com
Cigna - Dumb Password Rules
A max of 12 characters... Can't handle most symbols (only 5 supported). At least they have two factor auth via email or sms **sigh**
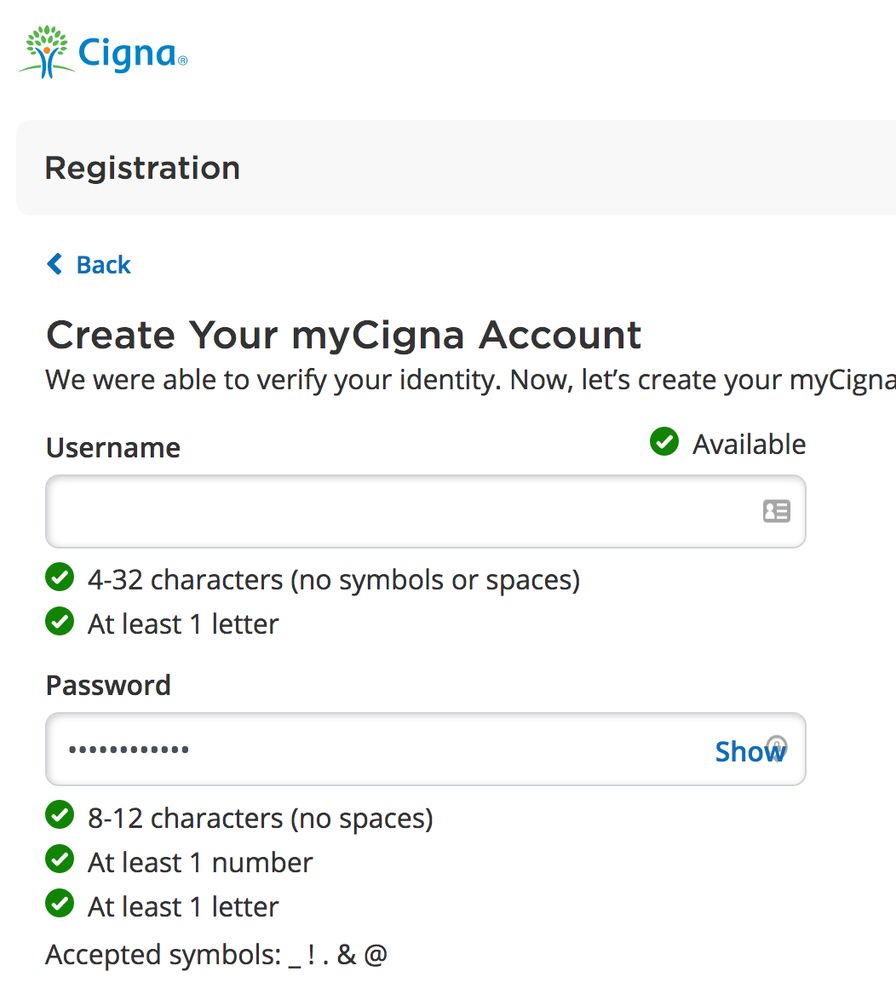
dumbpasswordrules.com
Cigna - Dumb Password Rules
A max of 12 characters... Can't handle most symbols (only 5 supported). At least they have two factor auth via email or sms **sigh**
social.skynetcloud.site
Original post on social.skynetcloud.site


dlvr.it
Toxic trend: Another malware threat targets DeepSeek
Introduction DeepSeek-R1 is one of the most popular LLMs right now. Users of all experience levels look for chatbot websites on search engines, and threat actors have started abusing the popularity of LLMs. We previously reported attacks with malware being spread under the guise of DeepSeek to attract victims. The malicious domains spread through X posts and general browsing. But lately, threat actors have begun using malvertising to exploit the demand for chatbots. For instance, we have recently discovered a new malicious campaign distributing previously unknown malware through a fake DeepSeek-R1 LLM environment installer. The malware is delivered via a phishing site that masquerades as the official DeepSeek homepage. The website was promoted in the search results via Google Ads. The attacks ultimately aim to install BrowserVenom, an implant that reconfigures all browsing instances to force traffic through a proxy controlled by the threat actors. This enables them to manipulate the victim’s network traffic and collect data. Phishing lure The infection was launched from a phishing site, located at https[:]//deepseek-platform[.]com. It was spread via malvertising, intentionally placed as the top result when a user searched for “deepseek r1”, thus taking advantage of the model’s popularity. Once the user reaches the site, a check is performed to identify the victim’s operating system. If the user is running Windows, they will be presented with only one active button, “Try now”. We have also seen layouts for other operating systems with slight changes in wording, but all mislead the user into clicking the button. Malicious website mimicking DeepSeek Clicking this button will take the user to a CAPTCHA anti-bot screen. The code for this screen is obfuscated JavaScript, which performs a series of checks to make sure that the user is not a bot. We found other scripts on the same malicious domain signaling that this is not the first iteration of such campaigns. After successfully solving the CAPTCHA, the user is redirected to the proxy1.php URL path with a “Download now” button. Clicking that results in downloading the malicious installer named AI_Launcher_1.21.exe from the following URL: https://r1deepseek-ai[.]com/gg/cc/AI_Launcher_1.21.exe. We examined the source code of both the phishing and distribution websites and discovered comments in Russian related to the websites’ functionality, which suggests that they are developed by Russian-speaking threat actors. Malicious installer The malicious installer AI_Launcher_1.21.exe is the launcher for the next-stage malware. Once this binary is executed, it opens a window that mimics a Cloudflare CAPTCHA. The second fake CAPTCHA This is another fake CAPTCHA that is loaded from https[:]//casoredkff[.]pro/captcha. After the checkbox is ticked, the URL is appended with /success, and the user is presented with the following screen, offering the options to download and install Ollama and LM Studio. Two options to install abused LLM frameworks Clicking either of the “Install” buttons effectively downloads and executes the respective installer, but with a caveat: another function runs concurrently: MLInstaller.Runner.Run(). This function triggers the infectious part of the implant.private async void lmBtn_Click(object sender, EventArgs e) { try { MainFrm.c__DisplayClass5_0 CS$8__locals1 = new MainFrm.c__DisplayClass5_0(); this.lmBtn.Text = "Downloading.."; this.lmBtn.Enabled = false; Action action; if ((action = MainFrm.O.__Run) == null) { action = (MainFrm.O.__Run = new Action(Runner.Run)); #

killbait.com
WWDC 2025, AI Updates, Chime IPO, and Cyberattacks Mark a Busy Week in Tech
This week’s major developments in the tech world included Apple’s announcements at WWDC 2025, the launch of new AI products, a major cyberattack, and a successful IPO. At WWDC 2025…

cyberlens.beehiiv.com
Cracked at the Core: How Ransomware Gangs Exploit SimpleHelp Flaws for Double Extortion Schemes
Inside the Tactical Playbook of Threat Actors Weaponizing Remote Access Software Vulnerabilities to Orchestrate Multi-Layered Extortion Campaigns

wardenshield.com
Think Like a Black Hat & Act Like a White Hat | WardenShield
Description:In today's digital battlefield, understanding both attack and defense is the key to cybersecurity mastery. Think Like a Black Hat & Act Like a White Hat takes you inside the minds of hacke...

techsparks.rebuscando.info
Week in Review: WWDC 2025 recap
WWDC 2025, AI Updates, Chime IPO, and Cyberattacks Mark a Busy Week in Tech

www.bleepingcomputer.com
Microsoft creates separate Windows 11 24H2 update for incompatible PCs
Microsoft confirmed on Tuesday that it's pushing a revised security update targeting some Windows 11 24H2 systems incompatible with the initial update released during this month's Patch Tuesday.

tinyurl.com
INTERPOL Dismantles Over 20,000 Malicious IPs Linked to 69 Malware Variants in Operation Secure
INTERPOL has dismantled more than 20,000 malicious IP addresses linked to 69 malware variants as part of Operation Secure. This operation aims to neutralize the infrastructure used by cybercriminals to spread malicious software.


tinyurl.com
New Malware Campaign Exploits Discord Invite System to Spread Skuld and AsyncRAT
A new malware campaign is exploiting a weakness in Discord's invite system to distribute an information stealer called Skuld and the AsyncRAT remote access Trojan. Attackers have hijacked links through vanity link registration, allowing them to silently redirect users from trusted sources to malicious servers. Check Point reported that the attackers combined ClickFix to execute this attack. The impacts include information theft and unauthorized access to victims' systems.

innovirtuoso.com
How to Protect Your Environment from the NTLM Vulnerability
Discover the risks associated with NTLM vulnerabilities and learn effective strategies to mitigate them. This blog post discusses the importance of auditing
www.wired.com
RFK Jr. Orders HHS to Give Undocumented Migrants’ Medicaid Data to DHS
Plus: Spyware is found on two Italian journalists’ phones, Ukraine claims to have hacked a Russian aircraft maker, police take down major infostealer infrastructure, and more.

www.darkreading.com
How Organizations Approach Security in the AI Era
LevelBlue research analyzes the rise of AI-powered threats, organizational preparedness, and the executive mindset around AI and cyber resilience.
cstu.io
Peak Performance Understated Power(1749940736268800)
Hyperlane is a lightweight and high-performance Rust HTTP server library designed to simplify network service development. It supports HTTP request parsing, response building, TCP communication, and redirection features, making it ideal for...



medium.com
Cosmic Downtime Simulation for Blockchain Resilience: Stress Testing the Immutable in a Mutable…
By Aditiya Widodo Putra, Cybersecurity & Blockchain Consultant